Home » Archives for May 2013
Wednesday, 29 May 2013
Tuesday, 28 May 2013
Command and Conquer 3: Kane's Wrath Gameplay
1. NOD Team: Black Hand (Me) and NOD
2. Scrin Team: Scrin and The Reapers faction
3. GDI Team: GDI and ZOCOM faction
4. GDI Faction Team: Two "Steel Talons" computer players
Enjoy and Subscribe! :D
CSS3 Animation Fundamentals Crash Course
Here’s a sample code that I will explain:
<!DOCTYPE html>
<html>
<head>
<style>
button {
position:relative;
animation:myanim 3s infinite;
-webkit-animation:myanim 3s infinite; /* For Safari and Chrome */
}
@keyframes myanim {
0% { background:orange; left:0px; }
25% { background:orange; left:200px; }
50% { background:orange; left:400px; }
75% { background:green; left:200px; }
100% { background:green; left:0px; }
}
@-webkit-keyframes myanim {
0% { background:orange; left:0px; }
25% { background:orange; left:200px; }
50% { background:orange; left:400px; }
75% { background:green; left:200px; }
100% { background:green; left:0px; }
}
</style>
</head>
<body>
<button>
I am alive! :D
</button>
</body>
</html>
CSS3 Animations basically depend on two things:
- animation (or -webkit-animation for Chrome and Safari web browsers) is used in the main element properties for selecting an animation sequence.
- @keyframes (or @-webkit-keyframes for Chrome and Safari) is used to set up the entire animation sequence.
In animation property we set the name of the keyframes where the sequence is defined called myanim, give the total duration as 3 seconds (3s) and tell it to run infinite times.
In keyframes section we tell it to change the color and set the position of the button from left side on each step. The steps themselves are in percentages denoting a stage each in the animation sequence. If only 0% and 100% were used then we could alternatively write from and to in their place because they mean the same.
This is just a simple example that will display a button jumping left-right on the page forever.
Monday, 27 May 2013
Cannot Comment on YouTube!
AFAIK only people on ‘non-Google Chrome’ browsers are facing this problem like on Firefox. On Firefox an add-on called Download Helper is causing this problem for many and disabling this add-on solves it. How ever this doesn’t work for all and some have made comments work by disabling ALL add-ons-- that is far from being a solution.
Another solution that works for some people is to not use any special character like :, ), $, #, @, etc., in comment and use only alphanumeric characters. Funny how commenting on YouTube has become an “experiment”.
This does seem to have some connection to new features YouTube implemented recently on their website and apparently is an unintentional non-compatibility with browsers and extensions. It may also be some issue with Firefox (like page rendering and loading problems on AdSense and Twitter faced by some Firefox users).
Meanwhile, Firefox users can temporarily use Chrome or any other browser for these things.
Sunday, 26 May 2013
Examples of New Elements in HTML5
CANVAS Tag
Painting on your webpage was never so easy and straightforward before. Now, such drawings can be made using Canvas tag -
<canvas id=”testCanvas”></canvas>
<script>
var canvas = document.getElementById(“testCanvas”);
var cContext = canvas.getContext(“2d”);
cContext.fillStyle = “#CECECE”;
cContext.fillRect(0, 0, 100, 100);
</script>
AUDIO Tag
Common audio formats like MP3 and OGG can easily be played using the audio tag. It shows a small audio player box with all the controls to conveniently start, stop, pause what’s playing.
<audio controls=”controls”>
<source src=”sample1.mp3” type=”audio/mpeg” />
<source src=”music/sample2.ogg” type=”audio/ogg”>
Sorry, your browser does not support AUDIO tag!
</audio>
DATALIST Tag
Now you can have a text field and a drop-down combo together by using DATALIST element. It looks like a simple text field at first but also shows an auto-complete list for whatever you’re typing.
<datalist id=”birds”>
<option value=”sparrow”>
<option value=”hawk”>
<option value=”parrot”>
<option value=”ostrich”>
<option value=”hen”>
</datalist>
VIDEO Tag
Videos are generally played on web pages using flash containers that require flash extension to be installed. But with the VIDEO tag the browser itself can play high-quality video.
<video width="320" height="240" controls>
<source src="movie.mp4" type="video/mp4">
<source src="movie.ogg" type="video/ogg">
Your browser does not support the video tag.
</video>
PROGRESS Tag
Not very frequently used but a progress-bar is something that has always been made using JavaScript and images. Now PROGRESS element takes it’s place because it’s just a one-liner to do the same.
<progress value=”43” max=”100”>
</progress>
As you can already guess, it’s value can be easily modified using JavaScript and it can be animated to show something being downloaded using AJAX, etc., a great addition to web-developer’s toolbox!
Wednesday, 22 May 2013
Win32 API - Code Sample to Know Drive Names
This code sample shows each drive letter in a message-box and also stores them in the “drives” array.
Number of drives found is stored in “drive_count” variable.
/******* Get all drives available *******/
char buffer[1024];
char *drives[10];
int drive_count = 0;
GetLogicalDriveStringsA(512, buffer);
for (int i = 0; i < 10; i++) { drives[i] = (char *) malloc(4); } // Allocate mem for 20 elements
char *ptr = buffer;
while (*ptr) {
MessageBoxA(NULL, ptr, "Drive", MB_OK); // Display each drive in a messagebox
strcpy(drives[drive_count], ptr);
drive_count++;
ptr = &ptr[strlen(ptr)+1];
}
for (int i = 0; i < 10; i++) { free(drives[i]); } // Free mem for drives
Saturday, 18 May 2013
How to Make Your Computer Fast for Gaming
This software is Razer Game Booster that can do all that for you and it is absolutely free. You can download it here:
http://www.razerzone.com/gamebooster
SQL Quick Reference
| AND / OR | SELECT column_name(s) FROM table_name WHERE condition AND|OR condition |
| ALTER TABLE | ALTER TABLE table_name ADD column_name datatypeor ALTER TABLE table_name DROP COLUMN column_name |
| AS (alias) | SELECT column_name AS column_alias FROM table_nameor SELECT column_name FROM table_name AS table_alias |
| BETWEEN | SELECT column_name(s) FROM table_name WHERE column_name BETWEEN value1 AND value2 |
| CREATE DATABASE | CREATE DATABASE database_name |
| CREATE TABLE | CREATE TABLE table_name ( column_name1 data_type, column_name2 data_type, column_name2 data_type, ... ) |
| CREATE INDEX | CREATE INDEX index_name ON table_name (column_name)or CREATE UNIQUE INDEX index_name ON table_name (column_name) |
| CREATE VIEW | CREATE VIEW view_name AS SELECT column_name(s) FROM table_name WHERE condition |
| DELETE | DELETE FROM table_name WHERE some_column=some_valueor DELETE FROM table_name (Note: Deletes the entire table!!) DELETE * FROM table_name (Note: Deletes the entire table!!) |
| DROP DATABASE | DROP DATABASE database_name |
| DROP INDEX | DROP INDEX table_name.index_name (SQL
Server) DROP INDEX index_name ON table_name (MS Access) DROP INDEX index_name (DB2/Oracle) ALTER TABLE table_name DROP INDEX index_name (MySQL) |
| DROP TABLE | DROP TABLE table_name |
| GROUP BY | SELECT column_name,
aggregate_function(column_name) FROM table_name WHERE column_name operator value GROUP BY column_name |
| HAVING | SELECT column_name,
aggregate_function(column_name) FROM table_name WHERE column_name operator value GROUP BY column_name HAVING aggregate_function(column_name) operator value |
| IN | SELECT column_name(s) FROM table_name WHERE column_name IN (value1,value2,..) |
| INSERT INTO | INSERT INTO table_name VALUES (value1, value2, value3,....)or INSERT INTO table_name (column1, column2, column3,...) VALUES (value1, value2, value3,....) |
| INNER JOIN | SELECT column_name(s) FROM table_name1 INNER JOIN table_name2 ON table_name1.column_name=table_name2.column_name |
| LEFT JOIN | SELECT column_name(s) FROM table_name1 LEFT JOIN table_name2 ON table_name1.column_name=table_name2.column_name |
| RIGHT JOIN | SELECT column_name(s) FROM table_name1 RIGHT JOIN table_name2 ON table_name1.column_name=table_name2.column_name |
| FULL JOIN | SELECT column_name(s) FROM table_name1 FULL JOIN table_name2 ON table_name1.column_name=table_name2.column_name |
| LIKE | SELECT column_name(s) FROM table_name WHERE column_name LIKE pattern |
| ORDER BY | SELECT column_name(s) FROM table_name ORDER BY column_name [ASC|DESC] |
| SELECT | SELECT column_name(s) FROM table_name |
| SELECT * | SELECT * FROM table_name |
| SELECT DISTINCT | SELECT DISTINCT column_name(s) FROM table_name |
| SELECT INTO | SELECT * INTO new_table_name [IN externaldatabase] FROM old_table_nameor SELECT column_name(s) INTO new_table_name [IN externaldatabase] FROM old_table_name |
| SELECT TOP | SELECT TOP number|percent column_name(s) FROM table_name |
| TRUNCATE TABLE | TRUNCATE TABLE table_name |
| UNION | SELECT column_name(s) FROM table_name1 UNION SELECT column_name(s) FROM table_name2 |
| UNION ALL | SELECT column_name(s) FROM table_name1 UNION ALL SELECT column_name(s) FROM table_name2 |
| UPDATE | UPDATE table_name SET column1=value, column2=value,... WHERE some_column=some_value |
| WHERE | SELECT column_name(s) FROM table_name WHERE column_name operator value |
Friday, 17 May 2013
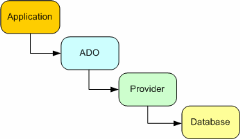
What is ADO.NET Connection String and How to Make It?
client.ConnectionString = “Initial Catalog=MyDatabase;Data Source=MyServer;Integrated Security=SSPI;User ID=Me;Password=MyPassword;”;
Here,
Initial Catalog is the database we are connecting to.
Data Source is the server on which database is running.
Integrated Security tells if we want a secure connection or not. Possible values: true (Windows authentication used), false, yes, no and SSPI (Security Support Provider Interface).
User ID is the database user ID for authenticating the connection.
Password is obviously the password for the User ID entered.
Of course this string could at first be assigned to a string variable and then entered into the ConnectionString property.
Wednesday, 15 May 2013
Windows Movie Maker in Windows 7
Windows Movie Maker is a very useful stock application from pre-Vista Windows versions (NT versions). A simple yet very useful video editing tool that can take care of basic to advanced video editing requirements.
With lots of video effects and transitions already available this provides one of the best freely available tool in this category. To apply transitions and titles in the beginning and/or end there is the timeline available. Music can be dragged and dropped on the timeline and stretched and tested as needed.
It is said that if your grandma can run it then it’s really easy. Windows Movie Maker is a tool that can be run by even laymen computer users without any special technical knowledge.
People who miss this amazing tool can download it for Windows 7/8 here:
http://windows.microsoft.com/en-in/windows7/products/features/movie-maker
As on the date of this post- on clicking the download button you will download the “Windows Essentials” downloader that when run will show several options that you can select to be installed. Among them is Windows Movie Maker as well. Check the ones you want to install.
Friday, 10 May 2013
Found this on Facebook - READ! - क़ुतुब मीनार का सच..
क़ुतुब मीनार का सच ..............
... असली नाम: विष्णु स्तंभ, ध्रुव स्तंभ
निर्माता: विराहमिहिर
विराहमिहिर के मार्गदर्शन में बना, सम्राट चंद्रगुप्त के शाशन काल केदौरानअसली आयु: २५०० साल से अधिक पुराना.--------------- ----------- 1191A.D.में मोहम्मद गौरी ने दिल्ली परआक्रमण किया ,तराइन के मैदान मेंपृथ्वी राजचौहान के साथ युद्ध में गौरी बुरी तरहपराजितहुआ, 1192 में गौरी नेदुबारा आक्रमणमें पृथ्वीराज को हरा दिया ,कुतुबुद्दीन,गौरी कासेनापति था. 1206 में गौरी नेकुतुबुद्दीन को अपना नायब नियुक्तकिया औरजब 1206 A.D,में मोहम्मद गौरी की मृत्यु हुईtab वह गद्दी पर बैठा ,अनेकविरोधियों को समाप्त करने में उसे लाहौरमेंही दो वर्ष लग गए.1210 A.D. लाहौर में पोलो खेलते हुए घोड़े सेगिरकर उसकी मौत हो गयी. अब इतिहासकेपन्नों में लिख दिया गया है कि कुतुबुद्दीननेक़ुतुब मीनार ,कुवैतुल इस्लाम मस्जिद औरअजमेर मेंअढाई दिन का झोपड़ा नामक मस्जिदभीबनवाई.अब कुछ प्रश्न .......अब कुतुबुद्दीन ने क़ुतुब मीनार बनाई, लेकिनकब ?क्या कुतुबुद्दीन ने अपने राज्य काल 1206से1210 मीनार का निर्माणकरा सकता था ?जबकि पहले के दो वर्ष उसने लाहौर मेंविरोधियों कोसमाप्त करने में बिताये और1210 में भी मरनेके पहले भी वह लाहौर में था ?कुछ ने लिखा कि इसे 1193AD में बनाना शुरूकिया यह भी कि कुतुबुद्दीन ने सिर्फ एकही मंजिल बनायीं उसके ऊपर तीन मंजिलेंउसकेपरवर्ती बादशाह इल्तुतमिश ने बनाई औरउसकेऊपर कि शेष मंजिलें बाद में बनी. यदि 1193मेंकुतुबुद्दीन ने मीनार बनवाना शुरूकिया होता तो उसका नाम बादशाहगौरी केनाम पर"गौरी मीनार", या ऐसा ही कुछहोता न कि सेनापति कुतुबुद्दीन के नाम परक़ुतुब मीनार.उसने लिखवाया कि उस परिसर में बने 27मंदिरों को गिरा कर उनके मलबे से मीनारबनवाई,अब क्या किसी भवन के मलबे से कोईक़ुतुबमीनार जैसा उत्कृष्ट कलापूर्ण भवनबनाया जा सकता है जिसका हर पत्थरस्थानानुसार अलग अलग नाप का पूर्वनिर्धारित होता है ?कुछ लोगो ने लिखा कि नमाज़ समय अजानदेने केलिए यह मीनार बनी पर क्या उतनी ऊंचाईसेकिसी कि आवाज़ निचे तक आभी सकती है ?सच तो यह है की जिस स्थान में क़ुतुबपरिसरहैवह मेहरौली कहा जाता है,मेहरौली वराहमिहिर के नाम परबसाया गया था जो सम्राट चन्द्रगुप्तविक्रमादित्य के नवरत्नों में एक , औरखगोलशास्त्री थे उन्होंने इस परिसर मेंमीनारयानि स्तम्भ के चारों ओर नक्षत्रों केअध्ययन केलिए २७ कलापूर्ण परिपथों का निर्माणकरवाया था.इन परिपथों के स्तंभों पर सूक्ष्मकारीगरी केसाथ देवी देवताओं की प्रतिमाएंभी उकेरी गयीं थीं जो नष्ट किये जाने केबादभी कहीं कहींदिख जाती हैं. कुछ संस्कृतभाषा केअंश दीवारों और बीथिकाओं के स्तंभों परउकेरेहुए मिल जायेंगे जो मिटाए गए होने केबावजूदपढ़े जा सकते हैं. मीनार , चारों ओर केनिर्माणका ही भाग लगता है ,अलग सेबनवाया हुआनहीं लगता,इसमे मूल रूप में सातमंजिलें थीं सातवीं मंजिल पर "ब्रम्हा जी की हाथ में वेद लिएहुए"मूर्ति थी जो तोड़डाली गयीं थी ,छठी मंजिल पर विष्णुजी की मूर्ति के साथ कुछ निर्माण थे. वहभी हटा दिए गए होंगे ,अब केवल पाँच मंजिलेंही शेष है.इसका नाम विष्णु ध्वज /विष्णु स्तम्भया ध्रुवस्तम्भ प्रचलन में थे, इन सब का सबसेबड़ा प्रमाण उसी परिसर में खड़ा लौहस्तम्भ हैजिस पर खुदा हुआ ब्राम्ही भाषा का लेख,जिसमेलिखा है की यह स्तम्भ जिसे गरुड़ ध्वजकहा गया है जो सम्राट चन्द्र गुप्तविक्रमादित्य (राज्य काल 380-414ईसवीं)द्वारा स्थापित किया गया था और यहलौहस्तम्भआज भी विज्ञानं के लिए आश्चर्यकी बातहै कि आज तक इसमें जंग नहीं लगा.उसी महानसम्राट के दरबार में महानगणितज्ञआर्य भट्ट,खगोल शास्त्री एवं भवन निर्माणविशेषज्ञ वराह मिहिर ,वैद्य राजब्रम्हगुप्तआदि हुए.ऐसे राजा के राज्य काल को जिसमे लौहस्तम्भस्थापित हुआ तो क्या जंगल मेंअकेला स्तम्भबना होगा? निश्चय ही आसपास अन्यनिर्माणहुए होंगे, जिसमे एक भगवन विष्णु का मंदिरथा उसी मंदिर के पार्श्व में विशालस्तम्भवि ष्णुध्वज जिसमे सत्ताईस झरोखेजो सत्ताईसनक्षत्रो व खगोलीय अध्ययन के लिए बनाएगएनिश्चय ही वराह मिहिर के निर्देशन मेंबनायेगए.इस प्रकार कुतब मीनार के निर्माणका श्रेयसम्राट चन्द्र गुप्त विक्रमादित्य के राज्यकलमें खगोल शाष्त्री वराहमिहिरको जाता है.कुतुबुद्दीन ने सिर्फइतना किया कि भगवानविष्णु के मंदिर को विध्वंस किया उसे कुवातु लइस्लाम मस्जिद कह दिया ,विष्णु ध्वज(स्तम्भ )के हिन्दू संकेतों को छुपाकर उन पर अरबी केशब्दलिखा दिए और क़ुतुब मीनार बन गया....
Learn Sanskrit Easily
Sanskrit was spoken by priestly and elite classes in ancient India and is still spoken by thousands of people (not as the main language but a literary or theological language). Today many scientific organizations are recognizing the straightforward and advanced qualities of Sanskrit that they did not find in any other language of the world! Sanskrit is proposed to be used in the development of higher level Artificial Intelligence and space contacts besides the primary use of galactic data processing.
Now you can also learn Sanskrit within a month by reading these eBooks provided totally free here. All the credits to it go to the author because I am just distributing them without any financial profits myself. Please download the RAR file here:
http://www.filesnack.com/files/c71pqkcd
Thursday, 9 May 2013
“We Are Anonymous” - The Essential Evil
How did it start?
Anonymous is not a mere “hacking group”-- it’s an idea that is vague but yet powerful. Originating from the image boards of 4chan during the years 2004-2007 where people posted pictures and texts anonymously this group got it’s basic form and strategy.
“Users of imageboards sometimes jokingly acted as if Anonymous was a single individual” [Wikipedia]
Giving this “group” a sense of unity in anonymity the idea went further when they started collectively pranking on habbo using identical avatars. These were however only casual stuff that became the origin of Anonymous.
A step further..
The so-called Project Chanology (“[4]CHANology” LOL) in the year 2008 pushed the group for the first time in the world of “hacktivism”. The word hacktivism is basically hacking and activism joined together that means activism through web hacking. Since, Anonymous consisted by now a considerable number of web developers, hackers, programmers, etc., naturally they thought of taking the online method of protesting against things a step further. It began with opposing the Church of Scientology and its activities. Anonymous conducted massive worldwide DDoS attacks against them.
However, by no means the group was only limited to cyber world only. Thousands of “Anons” (as they were called by then- short form of Anonymous), for instance, joined protests on 10th of February 2008 (Christian Era) before Church of Scientology worldwide. Here many of them came wearing Guy Fawkes Masks that became famous as a symbol of Anonymous later.
The rise to power
Anonymous emerged as a prominent hacking group by the year 2011 when it launched massive DDoS and hacking attacks on a number of government websites around the world as protests for different issues. For example, the attacks on the website of governments of Tunisia, Egypt, Syria, etc., to name a few.
Anonymous has also targeted the servers of MNC’s like Sony, PayPal, PostFinance, etc. and took them down for a good amount of time.
Ideology and Methods
Anonymous does not have a well-defined ideology or goal. It is like a flag- whoever can pick it up and carry it wherever he want. The active parts of group are generally from USA or Middle East- and of course from all parts of the world. The main theme of activity is the “Ops” like OpEgypt, OpSyria, OpPedo, etc., that basically defines a course of action. Participation is the basis of taking in members because there is no central authority to ‘admit” anyone into the group. Even the participation is by volunteering. The general convention is to start an “Op” against some evil activities happening somewhere (generally on a large scale) and once it gets some support and momentum more Anons come and join it.
The method of DDoSing is widely used by Anonymous because that’s what noob kids can do very well with a little bit of propaganda and very little technical knowledge (or effort). A very famous tool called LOIC (Low Orbit Ion Cannon) is used for sending thousands of packets to the target server to take it down. The funny name of this tool seems to have come from a computer game called Command and Conquer in which one of the factions called GDI uses a satellite beam weapon called Ion Cannon to obliterate and totally vapourize huge enemy bases.
Trend
Anonymous has recently become very fractioned (it WAS always fractioned) into groups with conflicting opinion. For example the infamous #OpIsrael seeks to “destroy the cyber space” of Israel because of its “oppression and killing of innocent Palestinians”. Now, if the real culprits are Israelis or the Palestinian terrorists relentlessly shooting missiles towards civilian cities in Israel is a very controversial matter. The Israeli so-called “occupants” are being told to “stop killing Palestinian women and children” who are the rightful holders of the landmass called Palestine by them.
I wonder if the Jews have been living on the said territory for thousands of years (called Canaan and Israel) how come the “Palestinian” Arabs be the owners. Most of the supporters of OpIsrael have been Muslims all around the world (even Bangladeshis and Pakistanis who themselves rape and murder Hindu, Buddhist, Christian and Ahmadiyya minorities in their countries).
The final word
Anonymous is a great asset to the common people given its fundamental goals and principles to save the common people from injustice. Sub-groups like LulzSec, AntiSec, etc., and supporting organizations like WikiLeaks have helped it grow into much more than a common “hacking group”. But the values are dying because of over-whelming incursion of selfish Islamic groups creeping in into it and using it for their own purposes. Also, many youngsters and even kids are fooled into supporting them just because they are “some cool hacking group” but they fail to see the difference between Good Ops and Bad Ops.
So, Anonymous is the essential evil that is like a storm against oppressors. But if the controls go into the hands of wrong masses it could take away the rights and harm the very people it was made to defend. Let us not the vision die.
And please-- for people guessing things-- I AM NOT ANONYMOUS.
Wednesday, 8 May 2013
To use ASP.NET WebForms or Model-View-Controller (MVC)?
The WebForms have been in use since several years now and is standardized by Micro$oft as its primary web dev platform. It has drag and drop functionality as the IDE provides the well-known toolbox. The drag and drop function works in the same way as in desktop .NET applications. Much of the initial code is generated automatically and the intellisense feature works perfectly on the server-side code mixed with HTML syntax.
But then a new way of coding ASP.NET websites emerged that looks very promising. It is called Model-View-Controller (MVC). Breaking away from the usual mixed up approach of WebForms (and even other webdev platforms like PHP), MVC tries the “division of labour” approach. In MVC the entire coding is logically divided into three kinds:
- Model means a template and basic structure over which the entire software is built. It is responsible for setting up database connections, file associations and remote resources that the application itself will be using/consuming during design and/or runtime. Using MVC we keep this part separate from others and usually this one is the first to be attended.
- View is the interface of the application. It is responsible for displaying information to the user and also taking input from the user. The interface should be easy to use and pleasing to see. MVC segregates this part from others so that the designer can work from the model up without worrying about any changes to the basic structure or any other additions.
- Controller (as the name suggests) controls the entire application and co-ordinates the Model with the View to provide a streamlined execution of the application. Controller in MVC is built according to the user interface and it often interacts directly with the components.
Here, page1 is actually name of a method and var1 and var2 are arguments to the method! The controller method will be something like this-
1: public ActionResult page1(string var1, string var2) {
2: ViewBag.Message = “Var1 = ” + var1 + “ and var2 = “ + var2;
3: return View();
4: }
Another question comes in the head- Is the page design also kept within that method itself? No. For this functionality “View” is used. The design for the controllers is made inside these views. They can have design with code embedded (no- there’s no “code-behind” stuff used in MVC sadly). For server-side code either of these two methods can be used- ASPX or Razor. However, they are beyond the scope of this article."So, which one should I use to make my website?" The answer is not very difficult. When there’s a big project with at least more than 3-4 people then MVC should be the ideal choice because it gives much better co-ordination in a team situation. However, when there is a small to medium level project that involves at most 1-3 people then WebForms should be fairly good for that.
Also, to mention database connectivity and passing data to the interface is a bit easier in WebForms than MVC. Many people get stuck while operating database in an MVC application because the contact of the model (database connector and data retriever often) and the view (interface) is rather sophisticated. Usage of LINQ however makes it a bit straightforward but surely most developers accustomed of using SQL commands and stored procedures will not like it at first site.
Tuesday, 7 May 2013
C# .NET Web Client Example (GET & POST)
GET requests hold data variables to be sent right there in the URL like:
http://www.example.com/index.aspx?variable1=somedata&variable2=otherdata
The POST variable on the other hand set these variable inside the HTTP Header like this:
POST /index.aspx
Content-Type: application/x-www-form-urlencoded
Content-Length: 38
variable1=somedata&variable2=otherdata
Using the System.Net.WebRequest class we can get the above functionality
First the GET request code:
string proxyString = "XXX.XXX.XXX.XXX"; // Some proxy
string URL = "http://www.example.com/index.aspx?variable1=somedata&variable2=otherdata";
System.Net.WebRequest req = System.Net.WebRequest.Create(URL);
req.Proxy = new System.Net.WebProxy(ProxyString, true);
System.Net.WebResponse resp = req.GetResponse();
System.IO.StreamReader sr = new System.IO.StreamReader( resp.GetResponseStream() );
System.Console.WriteLine( sr.ReadToEnd().Trim() );
Here,
- We define a proxy string that will be used later in the code. However, the “XXX” string is not valid here, just for example and the proxy is not used here as well.
- A URL is defined for GETting.
- A WebRequest object is created with the URL we defined.
- The true parameter tells the method that ‘no proxy is going to used here”.
- The GetResponse method uses the WebRequest object to access the URL and GET it and assign to a WebResponse object.
- We use the StreamReader to extract the data stream returned from the the request.
- The extracted data from the stream is printed on the screen.
1: string URL = "http://www.example.com/index.aspx";
2: string proxyString = "XXX.XXX.XXX.XXX"; // Not used
3: System.Net.WebRequest req = System.Net.WebRequest.Create(URL);
4: req.Proxy = new System.Net.WebProxy(ProxyString, true);
5: req.ContentType = "application/x-www-form-urlencoded";
6: req.Method = "POST";
7: string params = "variable1=somedata&variable2=otherdata";
8: byte [] bytes = System.Text.Encoding.ASCII.GetBytes(params);
9: req.ContentLength = bytes.Length;
10: System.IO.Stream stream = req.GetRequestStream();
11: stream.Write (bytes, 0, bytes.Length);
12: stream.Close();
13: System.Net.WebResponse resp = req.GetResponse();
14: if (resp != null) {
15: System.IO.StreamReader sr = new System.IO.StreamReader( resp.GetResponseStream() );
16: System.Console.WriteLine( sr.ReadToEnd().Trim() );
17: } else {
18: System.Console.WriteLine("Invalid Response Received :(");
19: }
Here many lines are same as in the GET request code. The ones that are unique I will elaborate here,
- We don’t add the GET parameters after the main address here because this is a POST request and variables will go inside the HTTP Header instead.
- Same
- Same
- Same
- We need to add this Header field to tell the web server this is a form we are sending and it should parse it that way. Basically we are fooling the web server to think we are a web browser.
- We mention that it is a POST request we are sending.
- We mention the POST variables to be sent with the header.
- We assign the parameter string to bytes. Check next point.
- We assign the size of params byte variable we just used to the POST request we are to send.
- Now we obtain a stream from the request.
- Write the entire data we have to the stream that takes it to the target web server.
- Close the stream that we are done with it.
- Get response from target server.
- Check if the response is not null.
- Same
- Same
- If the response is null then-
- Print an error message.
Monday, 6 May 2013
The Power of Shodan
Shodan is a new search engine like Google but specialized in one job. It can be used to find out unprotected servers, the ones with default passwords like “1234” or “pass” or whatever. It can be used to search for webcams, netcams, SCADA systems and much more! It is there for about 3 years now but not very popular with common people. It is however very popular with hackers who try to find out unprotected systems potentially vulnerable for hacking.
Shodan provides a very clean interface and one can expect good results on very simple search keywords like “default password”. It is sometimes eulogized with terms like “Google for Hackers”. It is crawling the web 24/7 and uses special methods to find its targets. Even amateur users can easily find out unprotected shop and office security cameras and see people moving about and ignorant about the fact that they are being watched on the internet.
Keeping its dark aspects aside, the site does not allow arbitrary searching by any visitor. To access search pages after the first one a user has to log in to Shodan. Registering there is totally free and they take no charges whatsoever for any search operations you do there.
If Shodan could also incorporate “generic” search capabilities like Google it well could become the top search engine. Now that we know about Shodan we should not think our domains are invisible if not not visible on Google search. Shodan is watching you!
The Twitter and The Turtle - Who’s the Slowest?
Twitter is the biggest social networking website besides Facebook that, according to recent stats on statisticbrain.com , has 55,47,50,000 members! You may also check out detailed reports at that link. Everyday on average 1,35,000 more users are signing up.
With this amount of traffic it is important to have a very good level of traffic handling. This is where the web masters of twitter are badly failing again and again. This is not a very young situation. It has been going on since at least a couple of years now. Though not justified yet comparing it to Facebook there is a big difference. Facebook users have never seen this much of slowness in page loading, etc. ever. It is also not unknown that Twitter frequently displayed traffic overload errors. This does not happen now.
The question is why twitter is experiencing such traffic overload problems. The answer could be found in the Twitter API’s that is used by numerous apps that update status of users without even opening the browser. Since Twitter allows updating a text message like status with limited characters its users hardly ever open their browsers for it. The apps they use instead can cause mass spamming and inefficient handling of tweets. It’s an irony that short text messages are supposed to generate lighter traffic naturally than uploading hundreds of images all day.
Facebook on the other hand is more suitable to be used on a browser. Also, Facebook users don’t update their every action during the day like “I am going to sleep”, “I am having a headache #wutthehell”, “lots of work #huahua” or “I love my dog” LOL. Since, FB is used more for sharing pics that are not updated as frequently as short text status. Also, Facebook provides a chatting feature that keeps many users busy when they are not updating their status. On Twitter however “chatting” is largely synonymous with “tweeting” and has a forum like approach. The difference and effects should be clear now.
Also, some people have pointed out flaws in the Twitter API itself that have been causing these slow loading problems. I am not sure about that but that could be the reason indeed.
As of today I logged in to tweet and it loaded fine without any slowness. I really hope guys there have solved this problem finally because we love Twitter a lot!
Sunday, 5 May 2013
How to install PAR::Packer in Strawberry Perl for Windows
To install PAR::Packer open a command prompt and type cpan into it. It will open a prompt where you have to write install PAR::Packer and press ENTER. It will download and install the module from CPAN.
Sometimes, Git installed in Windows causes path problems. Just go where the Git folder is (C: by default) and go into its bin folder and rename the file perl.exe to something else (I did perl.exe.bkp).
Friday, 3 May 2013
Lua – The Rising Star
While there are many scripting languages today including but not limited to Perl, Python, Ruby, etc., a scripting language that has gained lots of popularity in a very short time is Lua. It came as tiny and lightweight programming language especially targeted at games configuration language. It gained popularity especially through World of Warcraft game.
Lua is simple, has a negligible memory footprint and a very easy syntax that even n00bs can master (~cough~gamer kids~cough~). It is a scripting language that is run by the Lua interpreter. The interpreter is very tiny and has almost all the basic features a modern scripting language should have. The language itself was created in such a way that it is very easy to embed into a C program. In fact, when people require a scriptable, light and versatile language the first thing they prefer is Lua.
Let’s talk about its syntax-
- Lua loosely-typed language and variables can be used without any previous declaration. However, there is a local keyword that makes a variable limited to its current scope, that is if inside a function then only limited to that function. local also “defines” a variable in a way (in a very unobvious and unexpected way LOL).
- Lua has “quantitative” (I could not find another word for it) data types that is variables and tables (acts both as list and dictionary data types). The data types are automatically adjusted in the program.
- There are no braces in Lua and blocks are determined by do..end keywords. There is also no mandatory 4-spaces-before-indented-line thing in it like Python. Simple code statements can be written as one liners.
- Functions can omit open and closing brackets like in Perl when giving in parameters. Also, statements are not followed by semi-colons as in C/C++ or Perl and are terminated by a newline.
- Lua single line comments are like in SQL, just two dashes (--). However, multiline comments are much frowned upon by people since they are like (--[[ any comment here ]]--), that is we have to use 8 characters to make a multiline comment! God knows who gave this brilliant idea.
- The syntax looks like BASIC or Python but somewhat better than BASIC and more free than Python.
Lua has been taken by many people as a “n00b script” by many. But this is not the truth because it is faster than both Perl and Python. It might not have so many modules in its library like Perl or Python but it is growing. It looks very promising and we should give it some time to get stuff added to it. After all it takes some time for moon to rise in the sky before it gives light to a dark land.
Thursday, 2 May 2013
The Ghost of Windows XP
Windows XP was (is?) the most successful Windows version in the NT family. Now Windows 7 and Windows 8 are quickly removing it from the scene. But there was a time not very long back when OS meant Windows XP for most of the people around the world. A time when Linux wasn’t so popular and UNIX only ran in the servers. UNIX still runs in the servers only LOL but UNIX-like OS’s have spread a lot among common users and hackers (or developers) today.
Windows XP still can be seen in many big and small organizations especially businesses who don’t have time (or money) to change all their PC’s to Windows 7 or 8. XP is like a soul-mate to many and leaving it is like leaving an old trusted friend. Still Microsoft is going to end all it’s support to Win XP early this year and the PC’s that don’t move on will cease to get any more security updates and patches.
Many including me were stuck on XP for a good long time and very reluctantly let go of it. This is most applicable to gamers. Games like Battlefield 3 and Crysis 3 cannot be played on XP! You need Windows Vista onwards to play them. And these are just couple of games that I mentioned- there are more.
Another factor was the customizability and openness of XP that is not in Windows 7 with strict control over processes. This “openness” of XP was also the reason behind the never-ending malware infections. But the customizability factor that allowed theming of almost everything in XP is gone from Win 7. In Win 7 the “Start Button” is not easy to modify and a patched explorer.exe with modified Start Button graphic must replace the original one.
Now since everything has a beginning and an end, same is the truth for XP too. Windows 7 has many improvements over XP and there ARE workarounds to achieve XP like behaviour and look in 7. So, say a bye-bye to XP and welcome Windows 7 and 8.
Linux Terminal Crash Course
There are many not-so-well-known features of a linux terminal (I mean emulator terminal here not the plain one from old times). Several commands and keypresses can make your life really easy, especially if you are a sysadmin.
A good example of such a command is history. If you type history on terminal and press return, a list of commands you have run before opens. You can simply type a ! (exclamation mark) followed by the serial of the command you can see from the history that opened. This will run that command without you needing to type that all over again! Say for example there is a command perl -e 'print "hello world\n";' in the history and the serial # mentioned before it is 120. Then entering !120 on the terminal will run that command again. Sounds convenient?
Here's a list of several very useful Linux terminal shortcuts:
Virtual terminals
Ctrl + Alt + F1 - Switch to the first virtual terminal. In Linux, you can have several virtual terminals at the same time. The default is 6.
Ctrl + Alt + Fn - Switch to the nth virtual terminal. Because the number of virtual terminals is 6 by default, n = 1...6.
tty - Typing the tty command tells you what virtual terminal you're currently working in.
Ctrl + Alt + F7 - Switch to the GUI. If you have the X Window System running, it runs in the seventh virtual terminal by default in most Linux distros. If X isn't running, this terminal is empty.
Note: in some distros, X runs in a different virtual terminal by default. For example, in Puppy Linux, it's 3.
Command line - input
Home or Ctrl + a - Move the cursor to the beginning of the current line.
End or Ctrl + e - Move the cursor to the end of the current line.
Alt + b - Move the cursor to the beginning of the current or previous word. Note that while this works in virtual terminals, it may not work in all graphical terminal emulators, because many graphical applications already use this as a menu shortcut by default.
Alt + f - Move the cursor to the end of the next word. Again, like with all shortcuts that use Alt as the modifier, this may not work in all graphical terminal emulators.
Tab - Autocomplete commands and file names. Type the first letter(s) of a command, directory or file name, press Tab and the rest is completed automatically! If there are more commands starting with the same letters, the shell completes as much as it can and beeps. If you then press Tab again, it shows you all the alternatives. This shortcut is really helpful and saves a lot of typing! It even works at the lilo prompt and in some X applications.
Ctrl + u - Erase the current line.
Ctrl + k - Delete the line from the position of the cursor to the end of the line.
Ctrl + w - Delete the word before the cursor .
Ctrl + t - Switch 2 characters on a command line. If you typed sl, put the cursor on the l and hit ctrl+t to get ls.
Ctrl + b - Moves to the beginning of the previous or current word
Command line - output
Shift + PageUp - Scroll terminal output up.
Shift + PageDown - Scroll terminal output down.
clear - The clear command clears all previously executed commands and their output from the current terminal.
Ctrl + l - Does exactly the same as typing the clear command.
reset - If you mess up your terminal, use the reset command. For example, if you try to cat a binary file, the terminal starts showing weird characters. Note that you may not be able to see the command when you're typing it .
Ctrl+S Ctrl+Q - terminal output lock and unlock. These are simple shortcuts to pause and continue terminal output, works in most terminals and screen multiplexers like screen. You can use it to catch something if things change too fast, and scroll with Shift + PgUp PgDown. On linux console ScrollLock can also be used.
Command line - history
history - When you type the history command, you'll see a list of the commands you executed previously.
ArrowUp or Ctrl + p - Scroll up in the history and edit the previously executed commands. To execute them, press Enter like you normally do.
ArrowDown or Ctrl + n - Scroll down in the history and edit the next commands.
Ctrl + r - Find the last command that contained the letters you're typing. For example, if you want to find out the last action you did to a file called "file42.txt", you'll press Ctrl + r and start typing the file name. Or, if you want to find out the last parameters you gave to the "cp" command, you'll press Ctrl + r and type in "cp".
Sudo !! - Run last command as root
Command line - misc
Ctrl + c - Kill the current process.
Ctrl + z - Send the current process to background. This is useful if you have a program running, and you need the terminal for awhile but don't want to exit the program completely. Then just send it to background with Ctrl+z, do whatever you want, and type the command fg to get the process back.
Ctrl + d - Log out from the current terminal. If you use this in a terminal emulator under X, this usually shuts down the terminal emulator after logging you out.
Ctrl + Alt + Del - Reboot the system. You can change this behavior by editing /etc/inittab if you want the system to shut down instead of rebooting.
Since, most (if not all) Linux distributions come with friendly GUI interfaces, there are lots of terminal emulators out there. Which one you use depends on your preference. Some of them are:
- Gnome Terminal Emulator
- Konsole
- Xterm
- Rxvt
- Yakuake
How is Perl better than C?
As the title of this article already describes, today we will try to find out the features of Perl that make it better from C. Also, we will leave the points that make C better than Perl.
The first benefit of Perl over C is that since Perl is an interpreted scripting language and supported on almost all the standard operating systems, it is portable. C, natively, is dependant on the OS it is used for. It is possible to use a cross-compiler to write code from one OS for another OS. But the same code (99% of the time) cannot be used for any two OS's. There are bound to be platform based dependencies.
Secondly, Perl has lots of pre-written modules available for virtually every imaginable programming requirement. But in C, generally, one has to write everything from scratch. This massive Perl code repository is found on CPAN.
Perl can be "compiled" into a single executable using solutions like PAR::Packer and others. Though, this method does not actually "compile" the Perl code (actually it puts the interpreter and all the code to run it into a single executable) and is not very effective most of the time. This feature is growing with time.
Perl is easy to learn and use. With no compilation/linking required to run, it can be executed instantly. While C programs involve a compilation phase. This feature can have a small impact on Perl code being written faster than C code.
Perl syntax is considered more well-formed for text processing and parsing jobs. C does not have any benefits in this particular field. Also, the Perl special variables are very useful for quickly assigning and retrieving values of things that would require multiple lines of code in C. C does not have any such special variables or any similar features.
So, these (there are many more) are the benefits of Perl over C. Surely C language also has many benefits over Perl, one of them being that C can be (and is) used for developing systems level code like writing a complete OS. While Perl cannot (as yet) be used for making an OS. Also, compiled directly to machine code, C programs are considerable faster than Perl scripts doing the same job. This speed difference, however, may vary and could be surprisingly less in real production environments.
Both C and Perl have their benefits but there are few other programming languages that equal Perl in what it does best.
Windows 7 vs. Ubuntu 12.04 – The Faceoff!!
Surely the title does not justify itself in the eyes of many because ideally there is no comparison between Windows 7 and Ubuntu 12.04. Windows 7 is a “revolutionary” new (not much new now since Windows 8 is here already) development over Windows Vista that is looked upon as a (buggy?) transition from Windows XP. On the other hand Ubuntu 12.04 is the shining star in the Linux World. The favourite Linux flavour of most Linux users and probably the easiest Linux to install and use! So, lets make a point-by-point comparison of both (I know neither is going to win or lose but still)-
- Who Has More Users? Windows 7 has the largest user base in the entire world today followed by Windows XP and Windows Vista (Oh God, Why ??). Ubuntu has the greatest share of users in the Linux World that is not even close to Win7 but doesn’t actually matter because Linux people measure by quality and not quantity. Still, Windows 7 wins.
- Computer Games.. If you want to play all mainstream games with fantabulous graphics like Battlefield, Call of Duty, Far Cry, etc., you have to have Windows to play them. Linux is slowly growing after Windows in the gaming market but still has a long way to go. Not bad for a community maintained OS! But, Windows 7 wins.
- Ah, Malware! All Windows versions, whatever they claim, are prone to malware attacks. More so because the line between administrator and user is somewhat weakly marked. On the other hand Ubuntu (or any Linux flavour for that matter) provides stringent security measures and even smallest changes require password to be given at various places (not if you run as “root” LOL). This is a legacy from UNIX from which Linux gets its “spirit”. So, Ubuntu 12.04 wins.
- Where’s The Source? Windows 7 is a closed-source software. Nobody knows how does the Windows source code look like (or whatever super secret stuff Microsoft puts in it!). So, complete control on every aspect of it is practically impossible! On the other hand, Ubuntu 12.04 uses Linux kernel that is completely open-source. We can even compile and install the latest kernel ourselves. This gives us COMPLETE control over what runs on it and what not. We can even take the source code and add custom drivers and functionality to Linux ourselves. No doubt, Ubuntu 12.04 wins.
- The Looks.. Who Is Cutest? Windows 7 has an excellent GUI interface that looks very pleasing to the eye and is totally customizable in colour, images, tints, etc., aspects. Ubuntu 12.04 comes with Ubuntu desktop manager by default that is also very nice with an app bar on the left and the usual “Ubuntu-ish” taskbar on the top. But Ubuntu 12.04 is lot more customizable in the sense that we can install numerous desktop managers available for it like Gnome, KDE, XFCE or LXDE to name a few. Obviously, Ubuntu 12.04 wins.
- Need Some Software! Windows 7 has not thousands, but millions of software available either as legacy from Windows XP or before or even some made for Windows 8 (only 32bit ones) as well! On the other hand, while Ubuntu 12.04 also has a massive repository of applications it is still not equal to that of Windows. So, Windows 7 wins.
Okay, so there are still many more factors of confrontation between the two but since Microsoft does not even seem to acknowledge the existence of Linux (still I have heard Mr Gates “congratulating” Ubuntu maintainers once..) and Ubuntu guys don’t care about what-not qualities Windows has, I will close this article here.
After all, without Windows we cannot play our favourite games and without Linux no real hackers can survive. So, they have no comparison to each other. It’s like they are from different worlds and I really think so.